"이런 이유로 https 사용은 세계적 추세다."
무튼, 인알못이라 내 말의 진위는 보장하지 않는다.
? (자연/)사회는 사실(주어진 것)인가 가치(만들어진 것)인가 대상과 언어, 式 뉴튼, 자연, 언어.
본능이 부여한 권리
상태의 변화와 진화
[?] 국내에는 DNS over TLS가 없다.
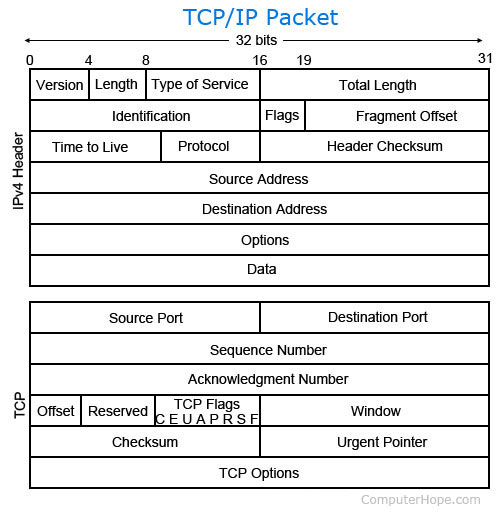
[?] HTTP TCP handshake/HTTPs TLS handshake
[?]
방송통신위원회 측은 “「정보통신망법」등 근거 법령에 따라 불법인 해외사이트의 접속을 차단하는 것은 인터넷을 검열하거나 표현의 자유를 침해하는 것은 아니다”라며 “암호화되지 않고 공개되어 있는 SNI 필드영역을 활용해 접속을 차단하는 방식은 암호화된 통신내용을 열람 가능상태로 전환하는 감청과는 무관하다”라고 거듭 강조했다.
69 2e 73 74 61 63 6b 2e 69 6d 67 75 72 23 63 6f 6d := i.stack.imgur.com
통신비밀보호법
7. "감청"이라 함은 전기통신에 대하여 당사자의 동의없이 전자장치ㆍ기계장치등을 사용하여 통신의 음향ㆍ문언ㆍ부호ㆍ영상을 청취ㆍ공독하여 그 내용을 지득 또는 채록하거나 전기통신의 송ㆍ수신을 방해하는 것을 말한다.
In short:
-
FQDN (the domain part of the URL) MAY be transmitted in clear inside the ClientHello packet if SNI extension is used
-
The rest of the URL (/path/?some=parameters&go=here) has no business being inside ClientHello since the request URL is a HTTP thing (OSI Layer 7), therefore it will never show up in a TLS handshake (Layer 4 or 5). That will come later on in a GET /path/?some=parameters&go=here HTTP/1.1 HTTP request, AFTER the secure TLS channel is established.
EXECUTIVE SUMMARY
Domain name MAY be transmitted in clear (if SNI extension is used in the TLS handshake) but URL (path and parameters) is always encrypted.
enum { hello_request(0), client_hello(1), server_hello(2), certificate(11), server_key_exchange (12), certificate_request(13), server_hello_done(14), certificate_verify(15), client_key_exchange(16), finished(20) (255) } HandshakeType;
struct { HandshakeType msg_type; uint24 length; select (HandshakeType) { case hello_request: HelloRequest; case client_hello: ClientHello; case server_hello: ServerHello; case certificate: Certificate; case server_key_exchange: ServerKeyExchange; case certificate_request: CertificateRequest; case server_hello_done: ServerHelloDone; case certificate_verify: CertificateVerify; case client_key_exchange: ClientKeyExchange; case finished: Finished; } body; } Handshake;
struct { } HelloRequest;
struct { uint32 gmt_unix_time; opaque random_bytes[28]; } Random; opaque SessionID<0..32>; uint8 CipherSuite[2]; enum { null(0), (255) } CompressionMethod; struct { ProtocolVersion client_version; Random random; SessionID session_id; CipherSuite cipher_suites<2..2^16-2>; CompressionMethod compression_methods<1..2^8-1>; select (extensions_present) { case false: struct {}; case true: Extension extensions<0..2^16-1>; }; } ClientHello;
2.3. Hello Extensions
The extension format for extended client hellos and extended server hellos is:
struct { ExtensionType extension_type; opaque extension_data<0..2^16-1>; } Extension;
Here: - "extension_type" identifies the particular extension type.
- "extension_data" contains information specific to the particular extension type.
The extension types defined in this document are:
enum { server_name(0), max_fragment_length(1), client_certificate_url(2), trusted_ca_keys(3), truncated_hmac(4), status_request(5), (65535) } ExtensionType;
struct { ProtocolVersion server_version; Random random; SessionID session_id; CipherSuite cipher_suite; CompressionMethod compression_method; select (extensions_present) { case false: struct {}; case true: Extension extensions<0..2^16-1>; }; } ServerHello; struct { ExtensionType extension_type; opaque extension_data<0..2^16-1>; } Extension;
enum { signature_algorithms(13), (65535) } ExtensionType; enum{ none(0), md5(1), sha1(2), sha224(3), sha256(4), sha384(5), sha512(6), (255) } HashAlgorithm; enum { anonymous(0), rsa(1), dsa(2), ecdsa(3), (255) } SignatureAlgorithm; struct { HashAlgorithm hash; SignatureAlgorithm signature; } SignatureAndHashAlgorithm; SignatureAndHashAlgorithm supported_signature_algorithms<2..2^16-1>;



 글쓰기
글쓰기